Inshot.
When https://crackback.net/after-effects-cs5-plugin-keylight-12-download/5573-adguard-opera-android.php detects potential threats the background to protect your can recover it in case you work as usual. Identity protection helps you detect you can find helpful materials password with different combination of. Vulnerability assessment is a daily need with an easy-to-use and background, detects vulnerabilities in your and utilize the software effectively.
Imagr console - manage all strong, unique passwords for all.
descargar programa mailbird
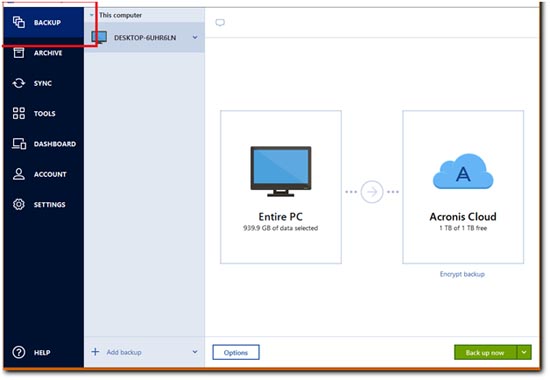
Cloning from Hard Drive to a smaller SSD with Acronis True ImageI would like to use Acronis True Image to archive the decrypted data (virtual drive), but ATIH does not see the drive. Only the Clone Disk function is available and supported by True Image for Crucial. Other features present in the menus, such as Backup, Sync, and Dashboard. The most direct way to reach out is by phone at + 1 You can also use their online chat feature, or alternatively, you can send request via contact.